How to setup ExchangeCore LDAP Authentication with concrete5?
In this post, I will cover the following topics.
- Create AWS Simple AD
- Launch Windows EC2 instance
- Setup remote desktop connection to the EC2 instance
- Configure Windows EC2 instance to manage AWS Directory Service
- Manage Active Directory domain on Windows Server
- ExchangeCore LDAP Authentication package install & configure on concrete5
- Basic operations of LDAP Authentication package
Now, let's start.
Create AWS Simple AD
If you don't have an AWS account, create one from here https://aws.amazon.com/resources/create-account/
- Login to the AWS Console.
- Go to Directory Services under Administration & Security.
- Click
Set up directory. - Next, choose the directory type. There are few types of directory but we will select Simple AD, which creates a new Active Directory Domain in AWS. If you want to know more about directory types please follow this link. https://aws.amazon.com/documentation/directory-service/
- Enter the details of the AD you want to create. Remember this information. You'll need it for the following steps.

- Directory type: Simple AD
- Directory DNS: auth.concrete5.co.jp [Use any domain name you want. Don't need to be a real one. Because it's only for internal use.]
- NetBIOS name: AUTH [You can use any short name for identifying it.]
- Default administrative user: Administrator [You can't change it.]
- Administrator password:
**********[Use a strong password, and must remember it.] - Confirm password: Confirm above password
- Description: Optional
- Directory size: small [You may choose as your need. For details, visit the following link named
Learn more] - VPC Details:
- VPC: You can select existing one or
Create a new VPC. Remember, you would have to create Windows EC2 (server) and UNIX EC2 (client) on same VPC. If you want to know more about VPC, please follow this link. https://aws.amazon.com/documentation/vpc/ - Subnets: No Preference [You can select if you've already created subnets or leave as No Preference. Remember, you need to select two subnets which is on different availability zones.]
ClickNext Step
- VPC: You can select existing one or
- Review the settings and click
Create Simple AD - Once your Simple AD is created, view the details in the console. Note that the two DNS addresses provided in the box below are two Amazon Elastic Compute Cloud (Amazon EC2) instances that have been created in your Virtual Private Cloud (VPC) are the domain controllers. Record these IP addresses–you’ll need them for a future step.
Launch Windows EC2 instance
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- From the console dashboard, choose Launch Instance.

- The Choose an Amazon Machine Image (AMI) page displays a list of basic configurations, called Amazon Machine Images (AMIs), that serve as templates for your instance. Select the
Microsoft Windows Server 2008 R2 Base. Notice that this AMI is marked "Free tier eligible."
- On the Choose an Instance Type page, you can select the hardware configuration of your instance. Select the t2.micro type, which is selected by default. Notice that this instance type is eligible for the free tier.

- Click
Next: Configure Instance Details - On
Step 3: Configure Instance Detailspage, input your preferences.
- Number of instances: 1- Purchasing option: Leave as default
- Network: Select the same VPC you used to create Simple AD
- Auto-assign Public IP: Enable
- Domain join directory: Leave as default
- IAM role: Leave as default
- Shutdown behavior: Leave as default
- Enable termination protection: Leave as default
- Monitoring: Leave as default
- Tenancy: Leave as default
- Advance Details: Leave as default
- Click
Next: Add Storage - Leave as default. Click
Next: Add Tags - Leave as default. Click
Next: Configure Security Group - Change the
Security group nameinto something readable (e.g. win-ad-sg) or leave as it is. ClickReview and Launch. - On the Review Instance Launch page, you may confirm if you have entered all informations correctly. Click
Launch. - When prompted for a key pair, you can select existing one or create new one.
Warning
Don't select the Proceed without a key pair option. If you launch your instance without a key pair, then you can't connect to it.
When you are ready, select the acknowledgement check box, and then choose Launch Instances.
A confirmation page lets you know that your instance is launching. Choose View Instances to close the confirmation page and return to the console.
It can take a few minutes for the instance to be ready so that you can connect to it.
For more, visit https://aws.amazon.com/ec2/getting-started/
Setup remote desktop connection to the EC2 instance
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- From running instances, select your newly created Windows EC2 instance. You may wish to change the EC2 name to identify it easily in next.
- Click on the button named
Connect. - Click on
Get Password. - You may choose the file path on your local computer, or can copy paste the contents into textarea.
- Click on
Decrypt Password. - You'll get the password. Save it for next use. We will use this password to login into the EC2 instance.
- Download and install the
Microsoft Remote Desktopfrom https://itunes.apple.com/us/app/microsoft-remote-desktop/id715768417. - Run
Microsoft Remote Desktopfrom applications. - Click on
+Newbutton. - New popup will appear. Input the following info.

- Connection Name: Whatever you want
- PC Name: The public IP of the Windows EC2 instance
- Gateway: Leave as default
- User name: Administrator
- Password: The password we got on step 7
- Followings: Leave as it is
- Close the popup window.
- A new entry will show on
My Desktops. - Select that and click
Start. - You'll be logged in to the remote desktop.
Configure Windows EC2 instance to manage AWS Directory Service
- Remote Desktop into the Windows server as above.
- Go to Start > Network > Network and Sharing Center > Local Area Connection > Properties > Internet Protocol Version 4 > Properties. Select Use the following DNS server addresses and enter the values of the addresses found in Step 7 above for your Simple AD and click OK.

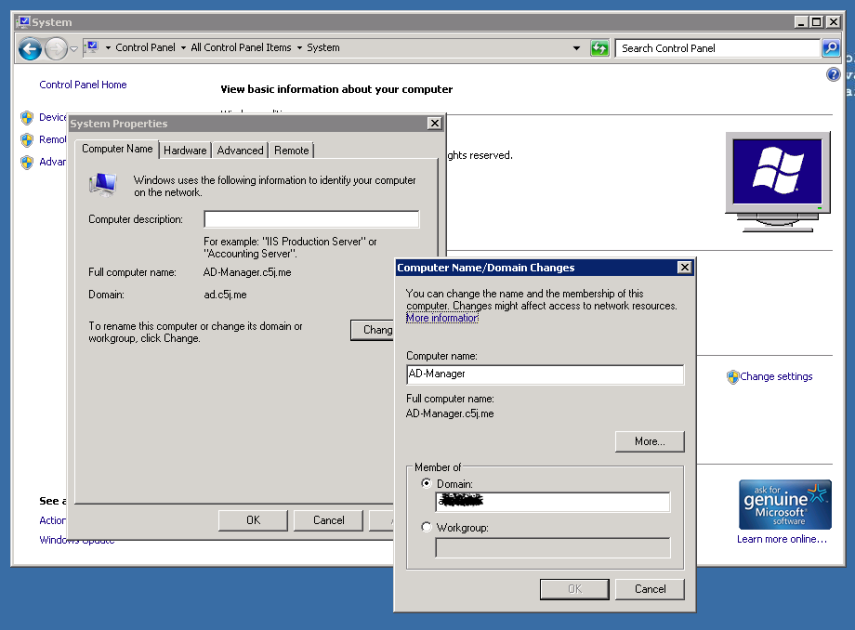
- Now we need to join this computer to the AWS Directory Service Domain. Go to Control Panel > System > Change Settings. Click Change to provide the domain this computer will be a member of (the domain entered in Step 5 above). You can also modify the computer’s workgroup or name to something more meaningful here if you would like, but it’s not required. Click OK.

- You will be asked for a username and password to complete this action. Use Administrator as the username and use the password you entered in Step 5 of creating Simple AD. Click OK. You should then receive a message saying “Welcome to the Domain.” Click OK and reboot your machine to finish joining the Domain.
Note: This is the domain administrator password, not the Windows password. - Open up Start > Administrative Tools > Server Manager.
- Select Features > Add Features > Remote Server Administration Tools.
- Install & restart.
Manage Active Directory domain on Windows Server
To manage active directory domain on windows server, we must need to login as domain administrator.
- Run
Microsoft Remote Desktopfrom applications. - Click on
+Newbutton. - New popup will appear. Input the following info.
- Connection Name: Whatever you want, e.g. Domain Manager
- PC Name: The public IP of the Windows EC2 instance
- Gateway: Leave as default
- User name: YourDomain\Administrator
- Password: The password you entered on Create Simple AD#Step-5
- Followings: Leave as it is
- Close the popup window.
- A new entry will show on
My Desktops. - Select that and click
Start. - You'll be logged in to the remote desktop.
- Open up Active Directory Users and Computers to manage the domain by going to Administrative Tools > Active Directory Users and Computers.
- In the left pane, double-click the domain. Click Users and add new user.
- Click Next. Type a password for each new user and record them somewhere. You’ll need them later when interacting with concrete5 LDAP Authentication.
- Uncheck User must change password at next login, click Next, and then click Finish.
- Right click on the user name and go to properties. Add email addresses for users. Because, to be authenticate with concrete5 LDAP authentication you must need an email.
ExchangeCore LDAP Authentication package install & configure on concrete5
- Launch another EC2 instance in same VPC to install concrete5. For more, please visit-
- Install & setup concrete5.
- Install
ExchangeCore LDAP Authenticationpackage. https://www.concrete5.org/marketplace/addons/exchangecore-ldap-authentication/ - Visit YourSite/index.php/dashboard/system/registration/authentication/ec_ldap/add
- Enter the details
- Basic Details
- Display Name: Whatever you want.
- Domain Access Account Username: username@domain [e.g. Administrator@auth.concrete5.co.jp]
- Domain Access Account Password: Password of the user
- LDAP Servers
- Hostname: The IP address you got on Create AWS Simple AD#step-7
- Port: 389 [You may need to open it from security group settings]
- Encryption: None
- Preferred Server Selection: In Order [As you want]
- Directory Type: Active Directory
- LDAP Schema, User Schema, Group Schema
- Use the button above named `Load Active Directory Setup. It'll load the default setup.
For more, visit https://docs.exchangecore.com/c5ldap/release/directory-configuration/
- Use the button above named `Load Active Directory Setup. It'll load the default setup.
- Basic Details
- Save It. If everything is fine, it will saved successfully.
- Enable LDAP authentication type from System & Settings > Login & Registration > Authentication Types.
- Now, logout and visit login page.
- Select LDAP authentication type and login with Active Directory user credentials.
Basic operations of LDAP Authentication package
Group Mapping
- Visit System & Settings > Login & Registration > Authentication Types > LDAP Directories > Your_Directory
- Click on Group Mapping
- Add Group Mapping
User Synchronization
- Visit System & Settings > Optimization > Automated Jobs
- Run
Synchronizes LDAP Users